Are you CMMC 2.0 Ready?
Empower your research with tiCrypt, developed in collaboration with the University of Florida by Tera Insights. Designed for secure research, tiCrypt meets ITAR, FISMA, and NIST standards. Confidently store, share, and analyze results securely in Vault storage or virtual machines. Deployed in national labs, medical centers, and R1 universities, tiCrypt ensures top-level data security. Take control and elevate your research security with tiCrypt.

No “pixie dust” promises of securing data
tiCrypt leverages strong symmetric and asymmetric cryptography to provide end-to-end encryption for secure file access, sharing, and processing.
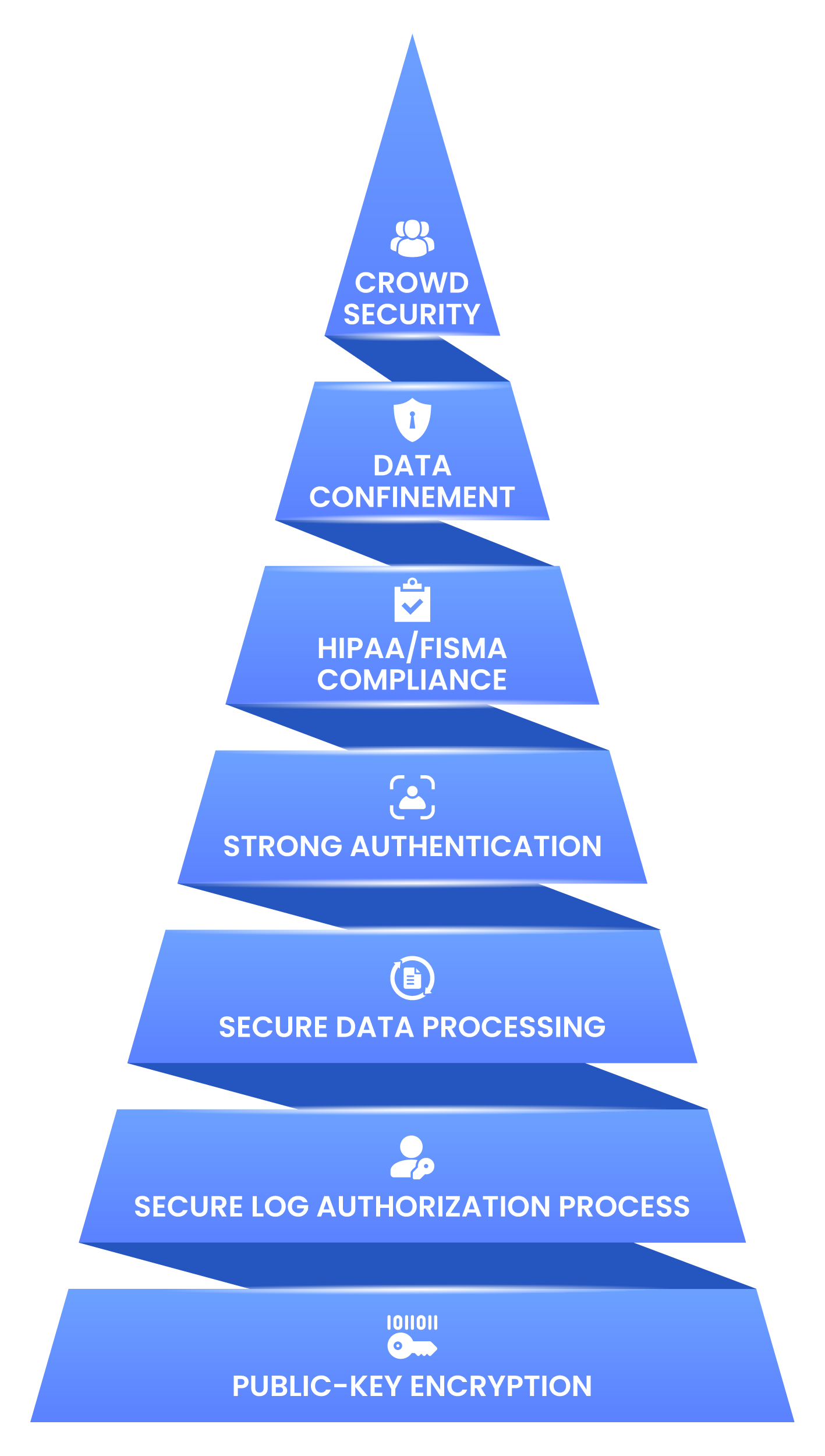
Public-Key cryptography is the foundation on which all security features in tiCrypt are built.
Public key encryption is at the core of all security mechanisms that guard the internet.
-
Allows checking the authenticity of a website through SSL certificates.
-
Allows establishing a secure communication channel with the web server.
-
Allows digitally signing messages, allowing for meeting audit and regulation requirements.
Developed for Researchers by Researchers
Crafted by researchers for researchers, tiCrypt acknowledges the unique and diverse workflows inherent in research projects. Thousands of hours of feedback from faculty, lab administrators, principal investigators, post-doc students, research computing staff, and university compliance officers at universities and medical centers shaped the development process. This collaborative approach ensures that tiCrypt is finely tuned to cater to the specific needs of the research community, providing a tailored solution for seamless integration into a variety of research workflows and processes.
Integrate tiCrypt with Existing Workflows
Enhance application workflows effortlessly with tiCrypt. Seamlessly integrate secure Virtual Machines into existing projects, fortifying data protection without disrupting established processes. Elevate your security standards with tiCrypt's advanced encryption, ensuring a confident defense against potential threats. Upgrade to tiCrypt for a seamless and secure data management experience.
Security First with tiCrypt
In the current compliance landscape, adherence to various policies and standards often translates into labor-intensive processes, involving multiple full-time equivalents (FTEs), paperwork, and manual risk control measures. tiCrypt revolutionizes this approach by establishing a robust security foundation grounded in a potent public-key infrastructure. Compliance is seamlessly achieved through automatic isolation and enforcement, eliminating the need for cumbersome manual procedures. With tiCrypt, universities and research institutions gain implicit control over the practical aspects of security, ushering in a new era of streamlined and efficient compliance management. Explore the benefits of tiCrypt's innovative approach across all facets of your organization:
-
tiCrypt, battle-tested in daily use by R1 Universities, Medical Centers, and National Labs, unlocks research growth opportunities, enabling universities to increase research expenditure and elevate national research rankings.
-
At the core of tiCrypt implementation is a commitment to strong security. tiCrypt never compromises data security, ensuring the integrity and confidentiality of your research data.
-
tiCrypt is easy to deploy and manage on existing or new hardware, eliminating the need for dedicated teams of full-time equivalents (FTEs) for support.
-
Built-in audit reporting simplifies workflows by providing automated auditing reports and system monitoring.
-
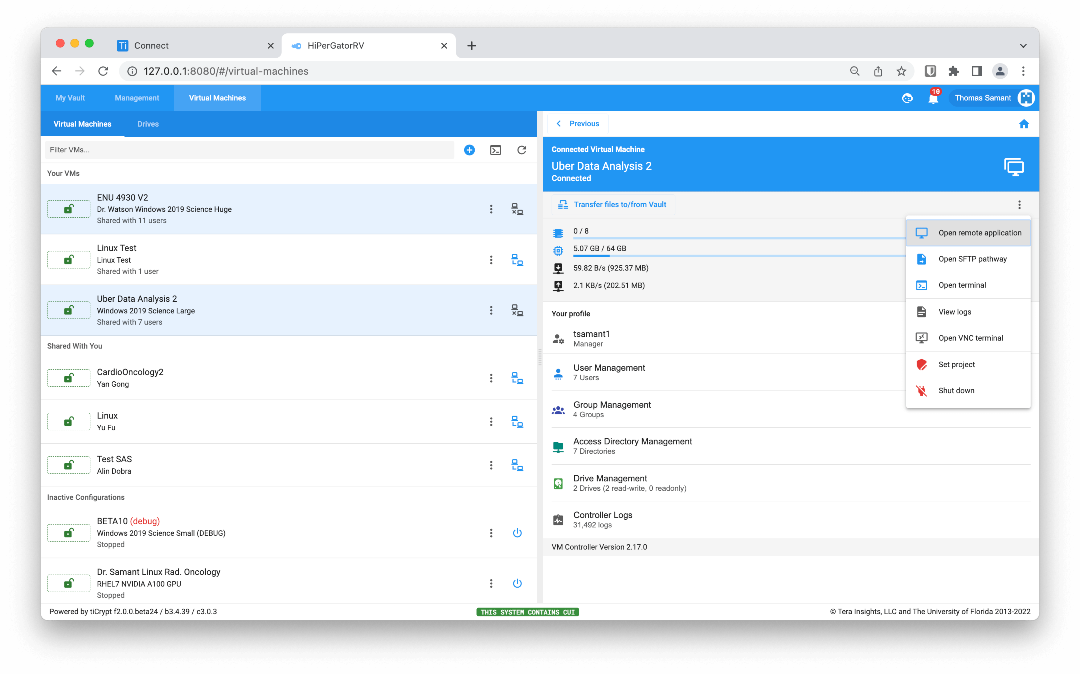
tiCrypt empowers researchers by allowing them to bring existing workflows into secure Linux and Windows VMs. Researchers have control over access and data workflows, eliminating the need to wait for system administrators to move data or grant permissions on the VM. Complex PuTTY and Xming workflows become a thing of the past with tiCrypt.
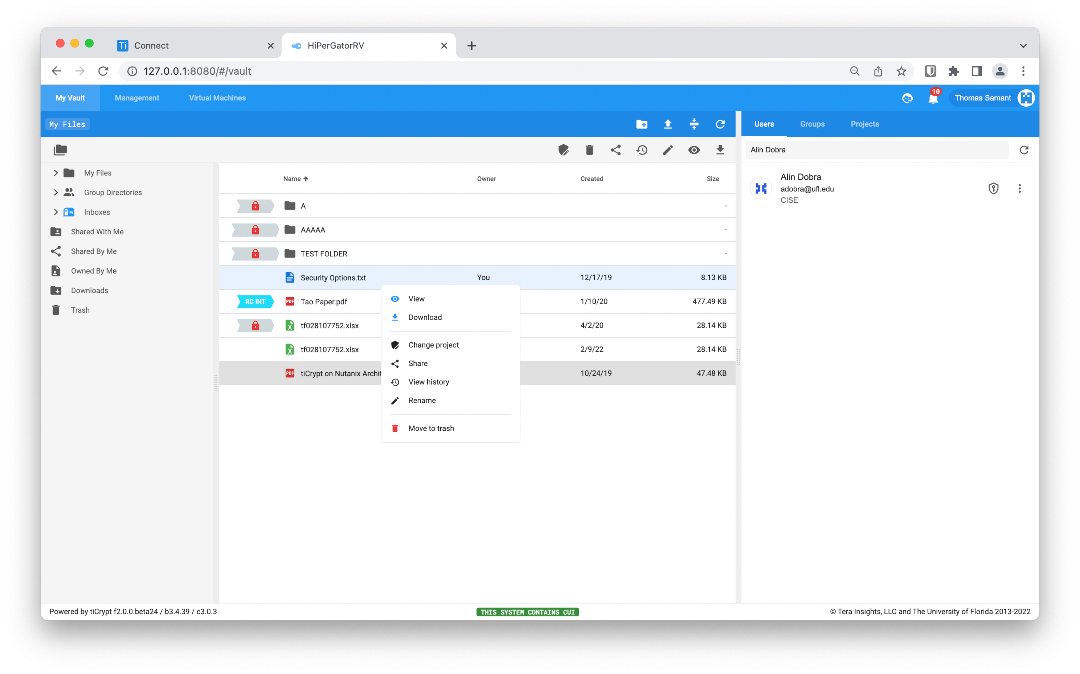
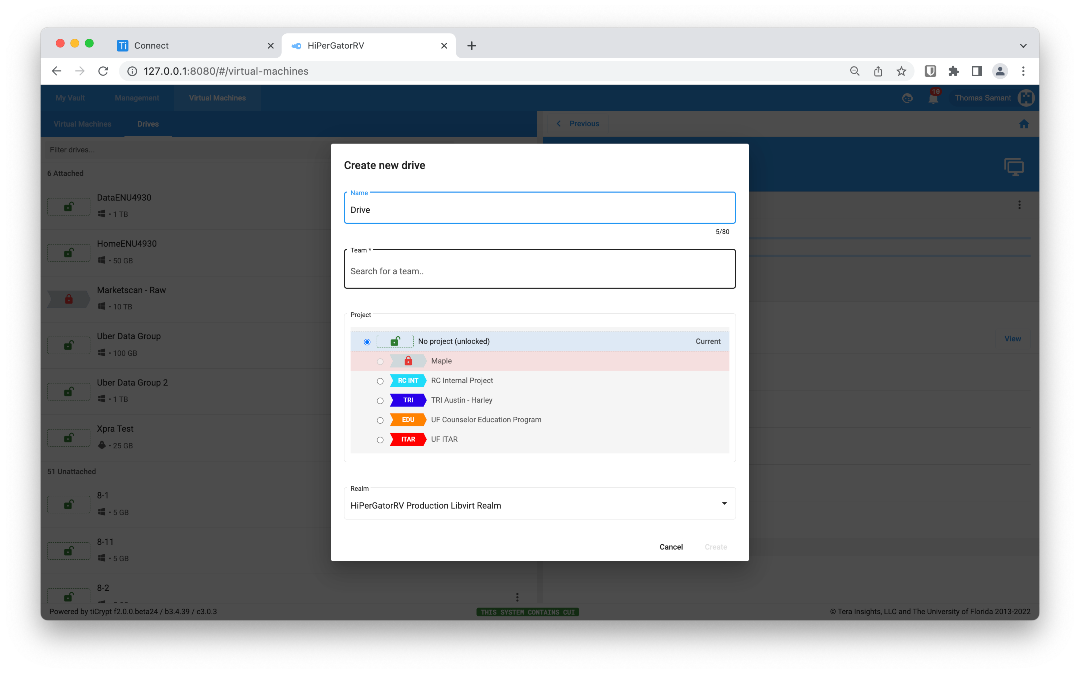
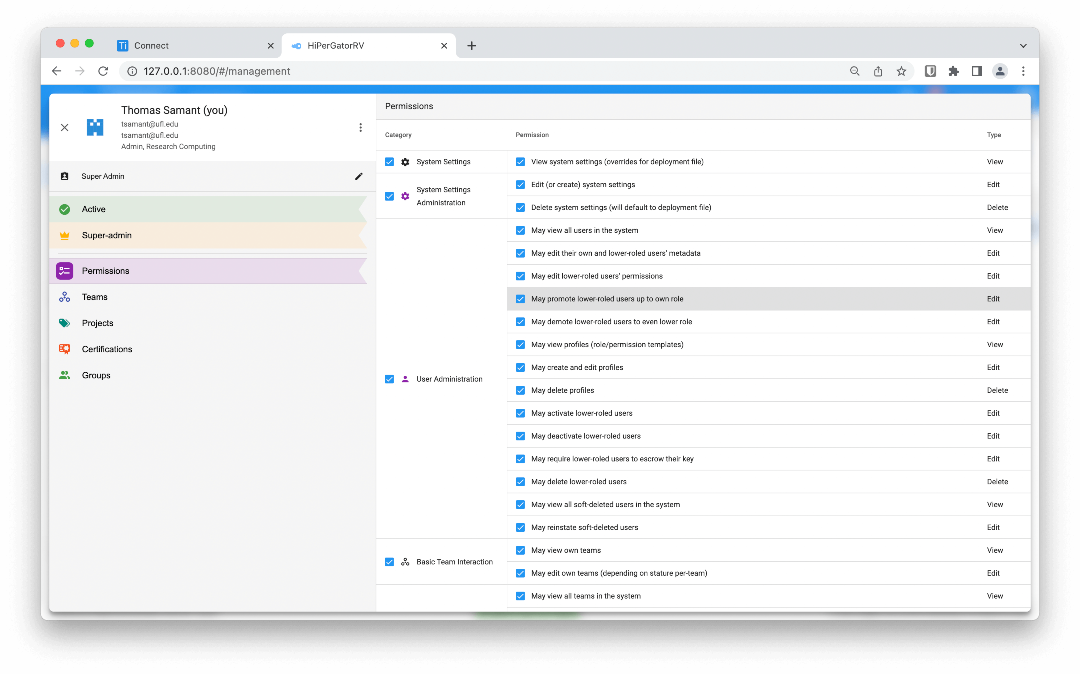
Have a look at how tiCrypt provides an easy-to-navigate web interface for researchers
Frequently asked questions about tiCrypt

Take Control of
Your Data
What Universities are saying about tiCrypt
Articles, Case Studies, and Papers